SOC - Security Operations Center
With our Security Operations Center (SOC), you will have continuous monitoring, early threat detection, and immediate incident response.
more infoShield your business before it's too late
Nowadays, cyberattacks are not just a possibility; they are a reality. Businesses across all sectors are exposed to constant threats that can compromise their information, reputation, and operations.
Digital threats are not science fiction; they are real and can jeopardize any business’s continuity. The question is not "Will I be attacked?" but rather "When will it happen, and how prepared will I be?"
At Andornet, in collaboration with Darkdata, we offer a suite of advanced cybersecurity solutions to ensure the comprehensive protection of your business in an ever-evolving digital world—one full of new opportunities but also new dangers.
Don't leave your business security to chance. With Andornet and Darkdata, you can shield your company before it’s too late. We protect what matters most: your infrastructure and the valuable information stored within it.
Proactive prevention We detect and neutralize threats before they affect your business.
Immediate response Our team of specialists ensures a swift and effective response to any incident.
Tailored services: We adapt to your company’s specific needs, creating a plan aligned with your operations and industry.
Comprehensive protection A combination of monitoring, intelligence, and auditing solutions to secure your digital assets.
DARKDATA All our cybersecurity services are backed by the expertise and technology of our partner, Darkdata.

With our Security Operations Center (SOC), you will have continuous monitoring, early threat detection, and immediate incident response.
more info
Information is power. Our cyber intelligence service enables you to stay ahead of attackers and protect your business. You’ll always be one step ahead.
more info
Through various system audit processes and ethical hacking techniques, we evaluate your infrastructure and network security to close vulnerabilities before attackers can exploit them.
more infoFind us at:
C/Prat de la Creu, 59-65. Esc. C, 3r G.
AD500 Andorra La Vella . (Principat d'Andorra)
From Monday to Thursday from 07:45 a.m. to 1:00 p.m. and from 2:00 p.m. to 6:00 p.m.
Friday from 8:00 a.m. to 3:00 p.m.
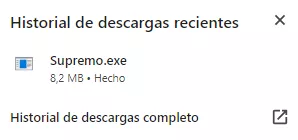
Click on the downloaded file.
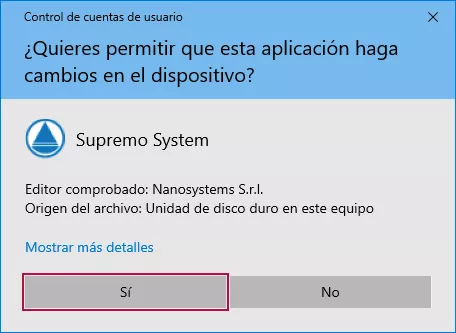
Click "Yes" to allow the installation.
Click to accept to connect with us